How do SOC 2 Compliance Software Vendors work?
SOC 2 compliance software vendors can make your SOC 2 journey easier, but how exactly do they do it?

SOC 2 compliance software vendors can make your SOC 2 journey easier, but how exactly do they do it?

Tens of thousands of dollars and hundreds of hours of time – a SOC 2 audit doesn’t come cheap or easy.
There is now a burgeoning market of SaaS companies out there to make the job easier and save employee time. Drata, Vanta, Carbide, Thoropass, Compyl, and Secureframe are just a few of the SOC 2 compliance software vendors in the space.
But how exactly do these platforms work to help you build your security program, make the audit process easier, and ultimately save your employees time? And just how many of the companies are there?
Several of our SOC 2 and ISO 27001 clients use these tools, and we’ve had the fortune to go hands-on with several of them. We’ve identified 9 key areas they can help companies succeed in their SOC 2 audits, along with one key limitation.
This article will dive into each of these areas, discuss the challenges that are presented to organizations and how a tool can help overcome them. We will also be using screenshots from, Carbide, Thoropass, and the Service Formerly Known as Tugboat Logic (now OneTrust Certification Automation) as illustrative examples of what these tools look like in action.
Please note that these screenshots were taken in late 2021 and early 2022 for OneTrust (formerly Tugboat Logic) and Thoropass because these two vendors gave us access to their platforms for the purpose of writing articles. Carbide sent us screenshots of their service to update this article. (We were not paid to highlight any of their platforms).
All of these compliance software vendors regularly update their services, so our screenshots likely do not 100% accurately reflect their current iterations, at whatever point you may be reading this in the future.
A compliance program is never an easy undertaking. Organizations that embark on one for the first time usually don’t even know where to start.
This makes it important for a SOC 2 compliance software tool to provide built-in guidance through the process of the SOC 2 audit, instead of just throwing the user into the deep end. While most vendors will provide customer success support to help in this matter as well, a tool built to logically guide and support the user through the audit process can help.
Carbide provides its guidance through a set of generic “Organizational Controls” to serve as the basis for the user’s security and privacy program. These controls explicitly map to the SOC 2 Trust Services Criteria.
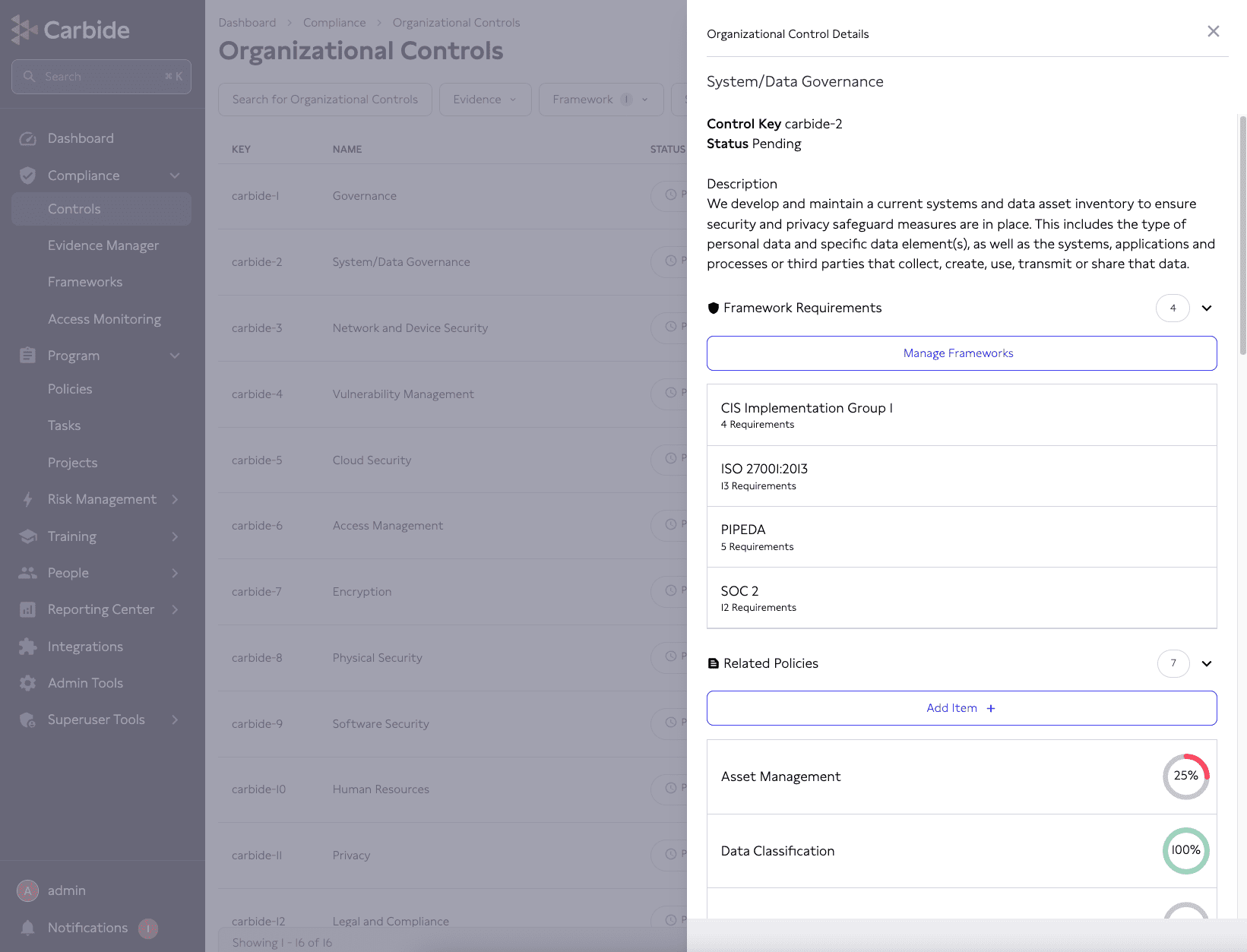
This sort of functionality is common across many (but not all) of the comparable SOC 2 tools. It’s worth knowing that no single tool is going to generate the perfect set of policies, controls, and evidence needed – some manual writing and revision work will be needed. But it does provide a solid foundation of tasks that the organization needs to complete to build towards their SOC 2 program.
Another near-universal feature of these SOC 2 compliance tools for guiding companies through the process is a dashboard view that lets users know how many tasks they have completed. Any tasks that the user or the tool creates are added to the total, and then progress bars are filled up automatically as the user completes tasks, making it easy to see at-a-glance where they are in the process.
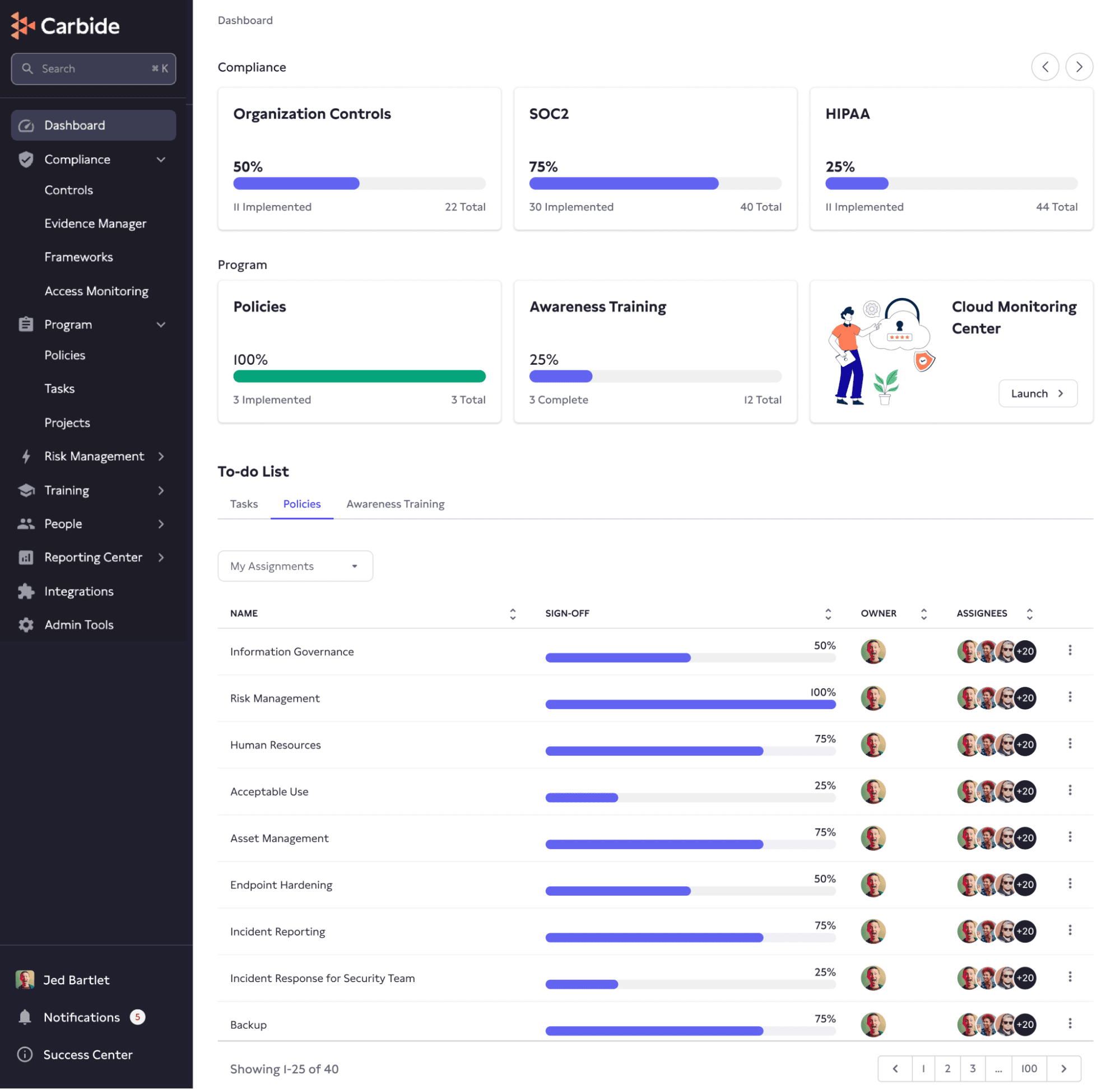
Going hand-in-hand with the point above, being tied to a SOC 2 control set is obviously vital for completing a SOC 2 audit – so all tools provide at least some tie!
The SOC 2 controls should be elegantly weaved into the whole system. It should be easy to find what controls a piece of evidence is used for, and it should be possible to view a list of all SOC 2 controls with their reference numbers and if any evidence has been allocated to them.
Providing strong, intelligent integration with SOC 2 controls along with multiple ways of viewing how evidence connects will make it much easier for users to understand their progress through the audit process.
OneTrust Certification Automation does this; each piece of evidence has a sidebar list of all controls it’s mapped to.
Then, each control has a sidebar list of reference codes it applies to.
Finally, it’s possible to get that nice, at-a-glance overview of all SOC 2 controls and their codes by clicking “Show SOC 2 COSO View” in the Audit Projects module.
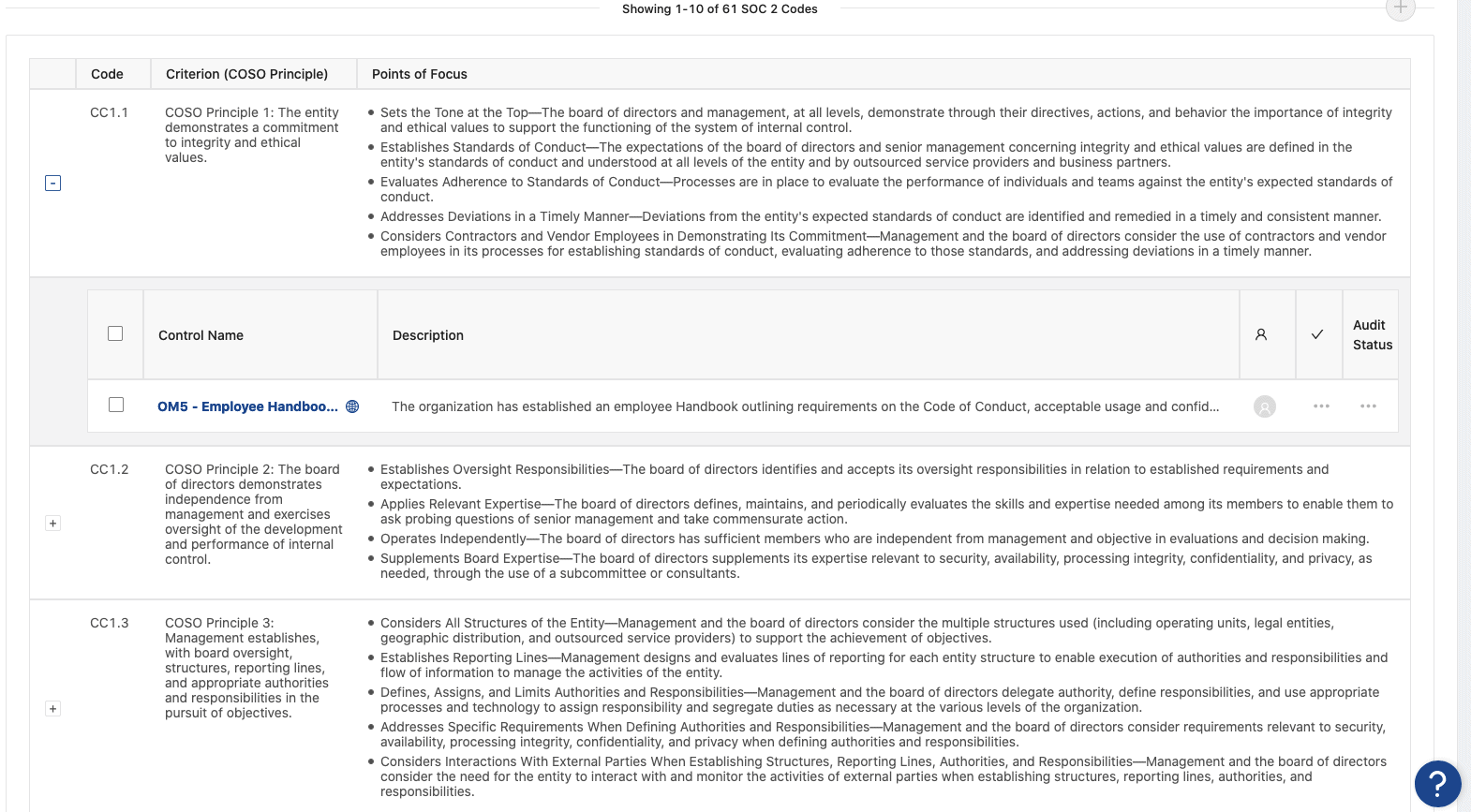
Documented security policies and procedures are the core of any cybersecurity program. Without them, there is no program. Writing policies from scratch takes an enormous amount of time and specialized knowledge, which companies pursuing a compliance audit for the first time are unlikely to have on their staff.
SOC 2 compliance tools can overcome this by providing a pre-written library of policy and procedure templates that their users can pick up and tweak for their purposes. Again, it’s unlikely that all of the policies will be perfect right away – some manual tweaking will be needed. But policy templates alone provide so much value to customers pursuing a compliance program.
So what do these templates look like in action? Most tools will automatically pull some selection of policies based on an initial survey or by the scope of the organization’s SOC 2 audit. They will also often provide a policy repository that users can browse and add to the security program as needed.
Where would most organizations be if they didn’t have Microsoft 365, Google Workspace, AWS, Google Cloud, Azure, GitHub, Jira, or any of the other dozens of tech services that go into supporting their operations?
These services are the real infrastructure of modern businesses, and they make a lot of jobs much easier. They do not, however, make cybersecurity much easier.
Each additional tool that a company stores data on needs to be accounted for and have its risks managed. Compliance audits mandate that data is proved from these tools to provide evidence that an organization has the proper security controls in place, but it’s a time-intensive process.
SOC 2 compliance tools can again save users’ time by providing direct integration with these services so that evidence may be pulled through and checked automatically for compliance with whatever policies and controls the user’s organization is attempting to meet.
For example, a SOC 2 compliance software tool could sync with a Human Resources Information System (HRIS), such as BambooHR, to sync the employee directory, ensure that former employees are having their access removed, and generate the evidence to document it.
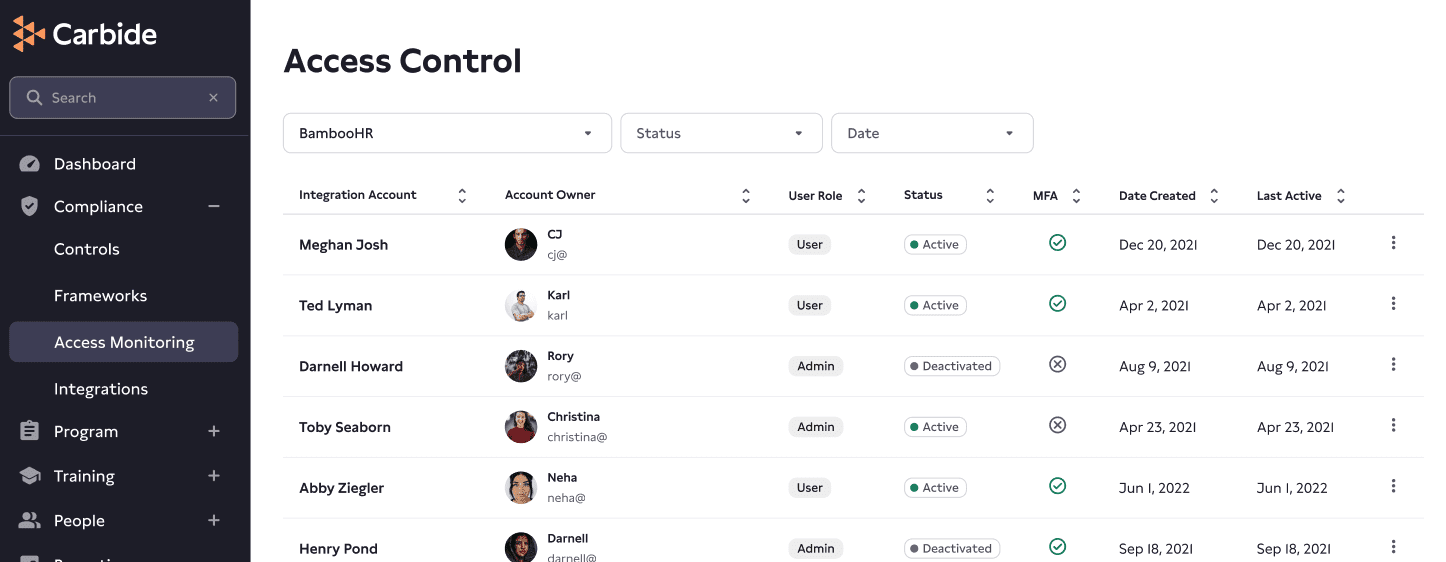
Below, you see what an integration page looks like in Carbide. Here, a user can review their BitBucket integration, tag the data it collects, and more.
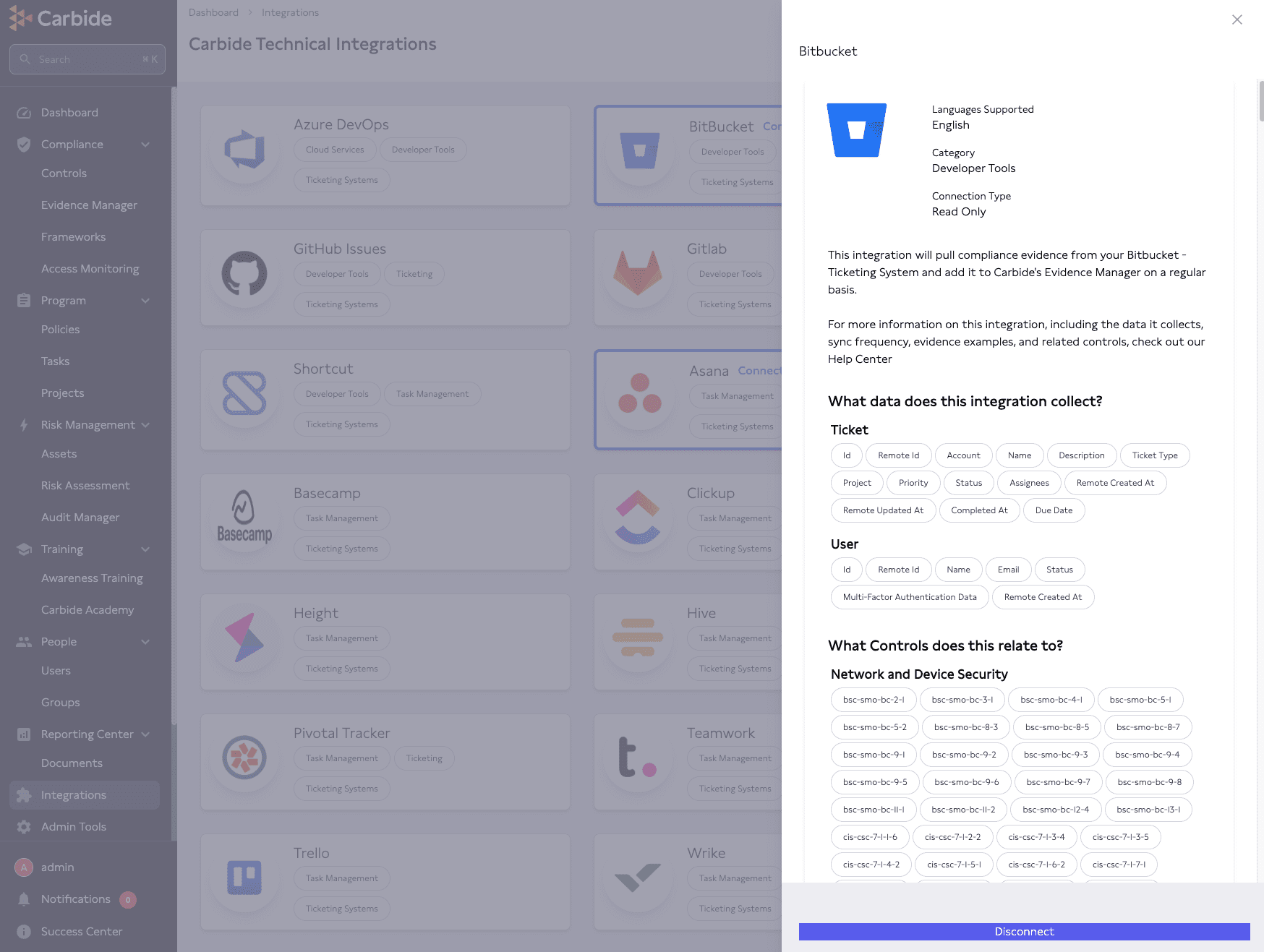
Automating evidence collection can provide massive time savings, but it would all go to waste if the tool couldn’t handle all evidence in a functional manner as well. Is evidence clearly versioned and dated, is it listed when it will be out-of-date – or previously went out-of-date? Is there an archive of historical data? Is the evidence linked to the appropriate controls?
Simply put, good tools will make it easy to find, review, update, and distribute evidence.
For OneTrust’s part, evidence management functionality revolves around Evidence Tasks. Evidence Tasks are generated based on policies, procedures, and controls the user has placed in their security program – and they can also be created manually when needed.
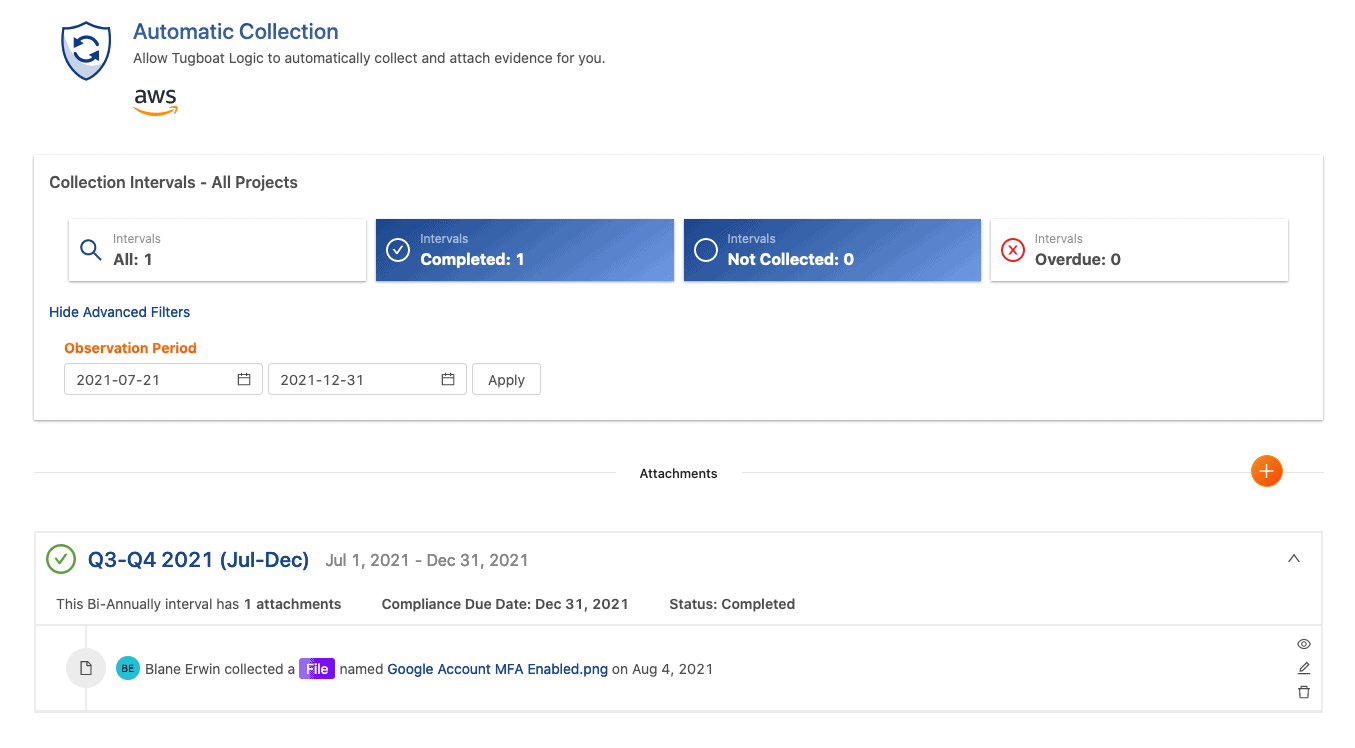
To complete an evidence task, just upload the required evidence to the piece within the time period and OneTrust will automatically mark it as completed. The evidence is then associated with whatever policy/procedure/control in the security program, and can be sent to an auditor when it’s ready for review.
Business demands might place a big emphasis on compliance, but cybersecurity is ultimately about risk management.
Risk assessments are important tools for guiding awareness of an organization’s security posture. Without taking the time to actually assess what risks an organization faces, it’s hard to know for sure how effective any security investment is going to be.
And after performing a risk assessment, the company must decide how risks are going to be managed. Again, these are hugely time consuming processes where tools can come in handy.
Most (but not all) of these vendors provide some level of risk management functionality because risk assessments are a required part of every compliance audit. Some tools are really just focused on creating the required material for the audit, while others provide more robust functionality for actually doing risk management work.
The most common risk management tools in SOC 2 compliance software solutions are risk surveys and risk registers. Pre-made risk surveys mapped to SOC 2 (or another compliance framework) are provided so that customers can fill it out and have a risk register generated based on their answers.
This provides a foundation for the risk register to be further customized based on the customer’s environment. SOC 2 will require that companies choose a risk treatment strategy (accept, avoid, mitigate, or transfer) for each risk. This has to be added to the register, along with the specific controls being used (if any).
A lot of manual work is usually needed here. There is no automating a true risk assessment. If people in an organization aren’t thinking critically about what risks they face, there is no real risk assessment happening.
When a company entrusts data and infrastructure to a vendor, that vendor’s security posture begins to directly affect their own. If they do everything else right but have a vendor who is lackadaisical about security, a breach is still likely to happen. As such, vendor risk management is another element of every good security program.
But it’s also another time-consuming one. It’s on each organization to email their own vendors and have them fill out lengthy security questionnaires (or have them send their own SOC 2 report), and to organize them. Here, a compliance tool can step in by providing a centralized location for performing vendor risk management tasks.
Ideally, the tools will allow users to create or upload risk questionnaires and send them from within the platform itself so that nobody needs to use an external email and manually upload the responses. Additionally, it should be possible to upload, link, and make comments on a SOC 2 if a vendor provides one.
Each vendor entry in the SOC 2 compliance software should have the ability to enter and describe the operational risk the vendor exposes the user to.
When we previously evaluated these tools, we were impressed by Thoropass’s strong vendor management functionality.
Notably, Thoropass does a lot to automate vendor management. They can integrate with some SSO providers to generate a list of all vendors being accessed through the organization’s entire SSO account. However, anything not caught by SSO will require manual entry.
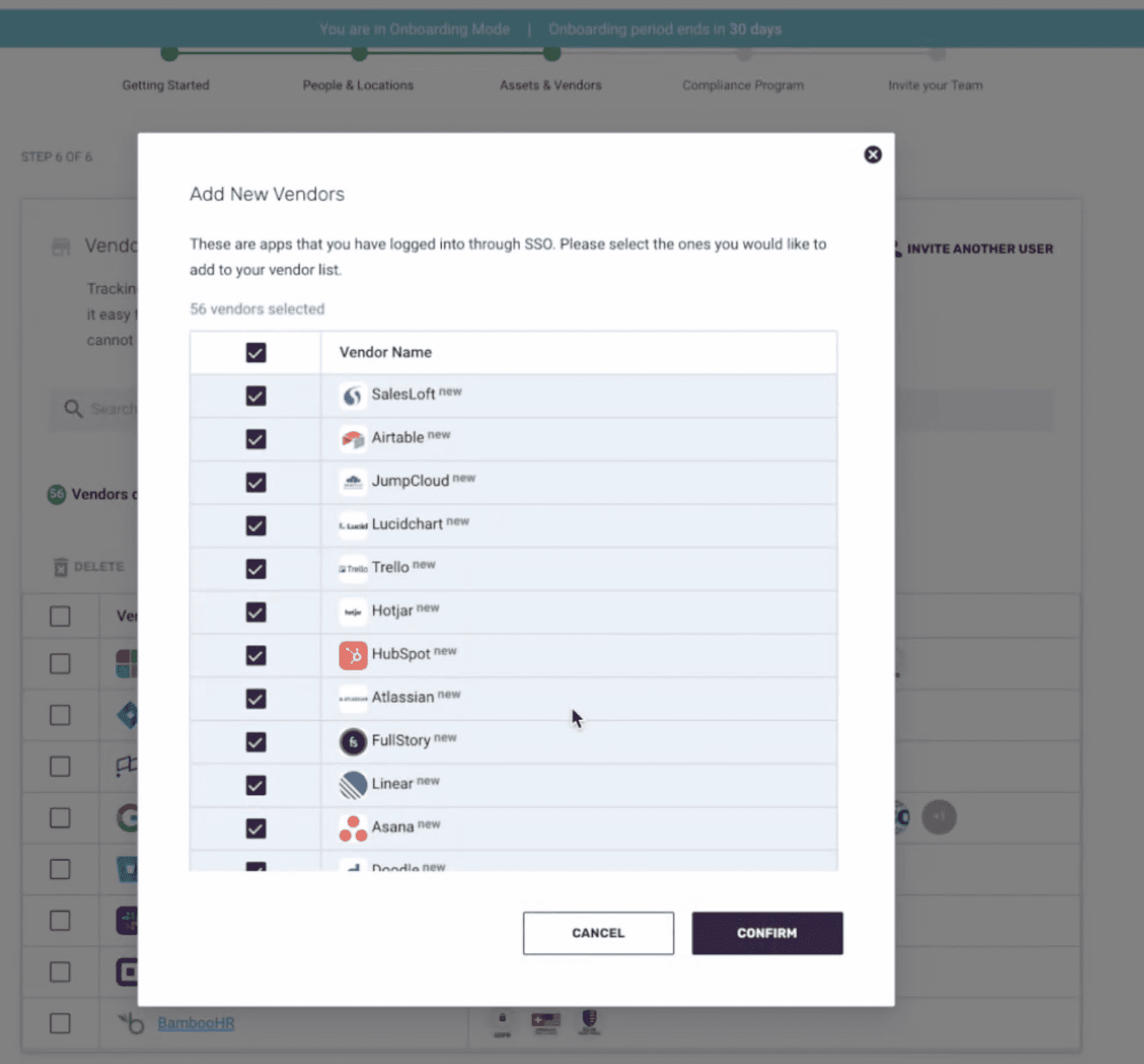
The next notable piece is that Thoropass has a compliance database, where they have records of what standards a given vendor is compliant with – and links are attached to make it easy for Thoropass’s users to grab their vendors’ compliance documentation.

After a company has put a compliance program in place and created a ton of evidence documenting it, they’re almost there! Now they just have to actually complete the audit.
Delivering information to and collaborating with an auditor is another challenging aspect of the compliance process, and it’s another that can be sped up with the help of a tool.
The ideal functionality of audit workflow tools is the ability to publish information to an auditor only when you are ready for them to review it and enable comments to be sent back and forth between your organization and the auditor so tasks can be completed as needed with transparency.
Carbide accomplishes this through its Audit Manager tool. Here, Carbide will auto-generate evidence requests associated with each individual SOC 2 control requirement. Evidence can be automatically attached if configured to do so, and otherwise can be manually uploaded to support each control item. Then, there’s a “Request Timeline” to track back-and-forth communications between the organization and its auditor.
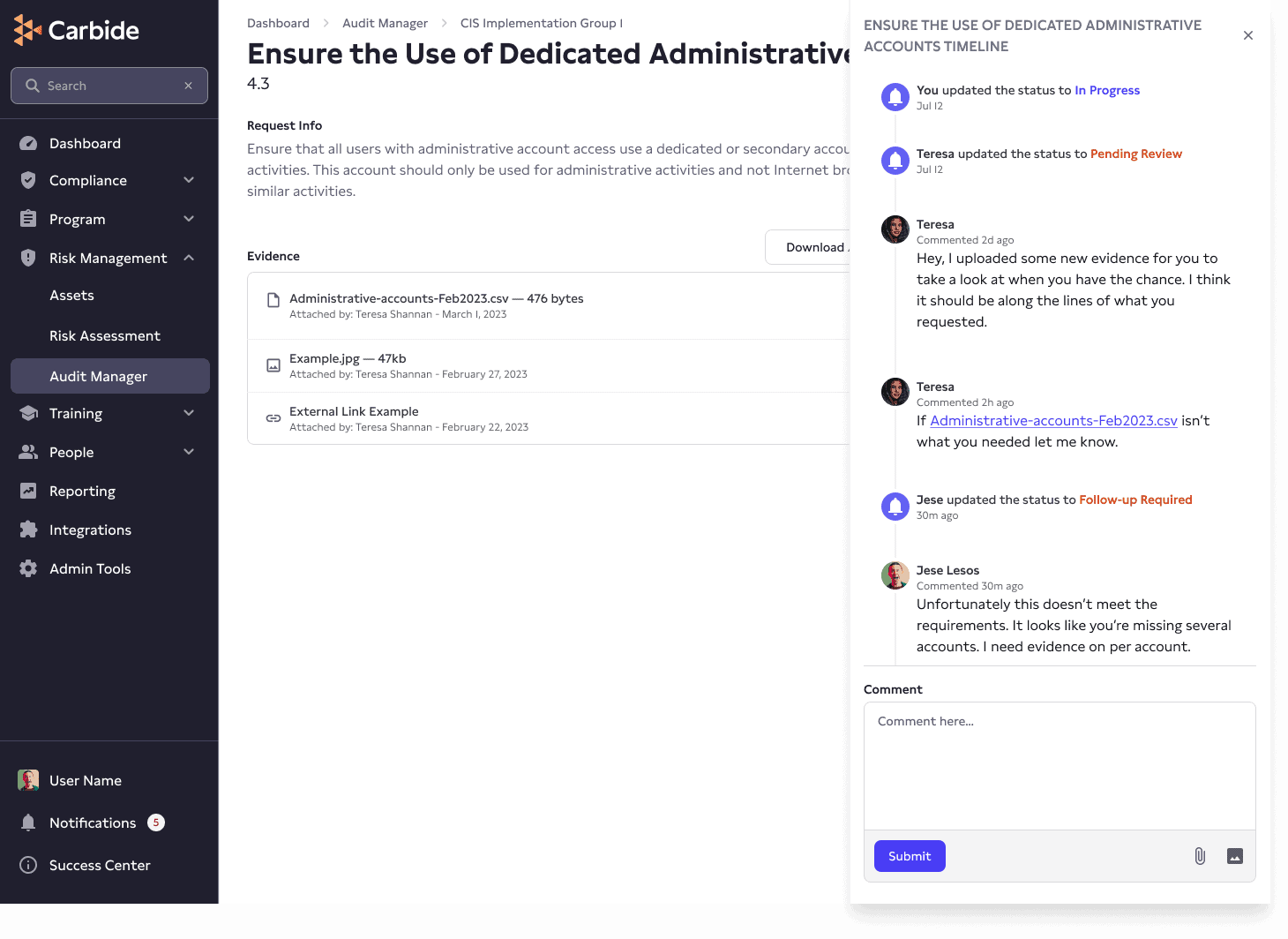
So you got your SOC 2. Congratulations!
Now you need to maintain your compliance program, or maybe add a new framework. Traditionally, this would be an enormous amount of work – new spreadsheets and all of the evidence needs to be reviewed and associated with the new controls.
But cybersecurity compliance tools can once again help out by automatically mapping existing evidence with the relevant controls of a new framework. While again, this is unlikely to be a completely perfect process, much time can be saved with a little bit of automation.
Getting an ISO 27001 or PCI DSS after doing SOC 2 isn’t going to be easy, but at least you’ll get started a lot faster at this point!
As with most things in life and business, there is no silver bullet to solve cybersecurity compliance. SOC 2 compliance software vendors like to say they can make it easy – and they do make it easier – but compliance projects still require heavy lifting from the organization taking them on.
Sometimes, these limitations just mean more, unexpected work, for the customers using these tools. Other times, these limitations may prevent users from successfully achieving SOC 2 compliance.
There are two main limitations of these tools:
1. They operate on the Pareto Principle.
2. Cybersecurity compliance requires organizational change.
The biggest limitation of SOC 2 compliance software solutions is that they operate on the 80/20 rule. A lot of tasks can be automated and made easier, but not all of them. They can generally get you 80% of the way there, but that last 20% can be really challenging to get right, and require expert help.
As mentioned earlier, the manual work required in risk management is a great example. An automated risk survey will generate a risk register for companies to start working off of – but it won’t be a comprehensive or compliant risk register. An actual person is going to have to add any missing risks, decide how to treat those risks with the cybersecurity program, actually roll out the cybersecurity controls, and track that in the tool.
In a small organization without a full-time cybersecurity employee, this is usually going to fall on the CTO. They will save time relative to doing it all manually, but it will still require a significant amount of work. Additionally, they may not have the cybersecurity expertise needed to know what controls to use to treat a given risk.
And this is just one example! A lot of manual work is going to be needed to turn templates into great policies and track information about each vendor.
Most SOC 2 compliance software vendors will have customer success teams to help, but they won’t have the same depth of knowledge and experience full-time cybersecurity leadership would.
You can’t become SOC 2 compliant just by saying that you’re doing the right things. Your organization must actually have a functioning cybersecurity program put into practice. For organizations pursuing their first SOC 2, this almost always requires a significant amount of organizational change.
A software tool is not capable of rolling out new procedures and practices in a company. New tools, new training, and so much more has to be rolled out to the organization. Only an informed and empowered leadership team can drive the kind of change needed to succeed.
Ultimately, these software solutions are just tools that require experts to use them to succeed. Not all organizations have the cybersecurity expertise needed to create a compliant program and drive its adoption available – or maybe the CTO just doesn’t have the bandwidth.
Thankfully, these tools can be supplemented with outside help. Our vCISO-led cybersecurity teams have helped many organizations who use Thoropass, OneTrust, Vanta, Drata, and more successfully achieve their SOC 2 compliance.
There are a lot of SOC 2 compliance software vendors, so this list may not be exhaustive. It represents the vendors we are aware of, as of the publication date of this article (March 2023).
Cybersecurity programs take time. No software tool is going to be a magic bullet that delivers a SOC 2 attestation in just a few weeks.
However, they can provide immense value in helping a company get compliant, stay compliant, and run a top-notch cybersecurity program – all while saving employees’ time along the way.
The cost of SOC 2 compliance can vary based on several factors, such as the scope of the audit, the audit vendor, the size and complexity of the systems and controls in the organization, and the chosen compliance provider. On average, small to medium-sized businesses might incur audit costs ranging from $20,000 to $50,000 while larger enterprises with more extensive requirements could face costs up to or exceeding $100,000. Please note: these cost estimates are for the audit alone and may not include the professional fees to obtain compliance.
Achieving SOC 2 compliance is a collective responsibility involving multiple members of an organization, including leadership, IT teams, legal, HR, and often, third-party consultants. To streamline this intensive process, organizations can engage a Virtual Chief Information Security Officer (vCISO), an experienced cybersecurity professional, to lead the compliance efforts. The vCISO plays a crucial role in ensuring the organization aligns with SOC 2 standards.
SOC providers, also known as System and Organization Controls providers, are normally staff or virtual CISOs who work toward ensuring compliance. SOC providers monitor networks, inform business leaders of potential threats, monitor and address vulnerabilities, prioritize security operations, and respond to cyberattacks. Additionally, SOC providers conduct audits and assessments to guide businesses through the process of achieving and sustaining compliance with SOC standards, such as SOC 1, SOC 2, and SOC 3.
 5 min read
5 min read
 5 min read
5 min read
 5 min read
5 min read
© 2025 All rights reserved
Only 1/3 of cyber insurance policies actually pay out in incidents. Most companies have cyber insurance policies that insure too little, or too much, and have absurdly low caps and silly exclusions.
To learn more about cyber insurance and determine if you have the right coverage for you, join us for a free vCISO Office Hours session on Tuesday, April 18 at 1 p.m. eastern time. Bring your questions!
Getting ready for your first SOC 2? This eBook is full of actionable advice to help you prepare for and succeed in your first SOC 2 audit.
Learn:
