There are many blog posts, articles, training materials and all sorts of content admonishing people to pick good passwords. But there is not nearly the same volume of content discussing good username selection. Administrators especially should be cognizant of good usernames to reduce the risk of an attack.
Here at Fractional CISO we took a look at a week’s worth of failed logins on our website and the username distribution is stunning.
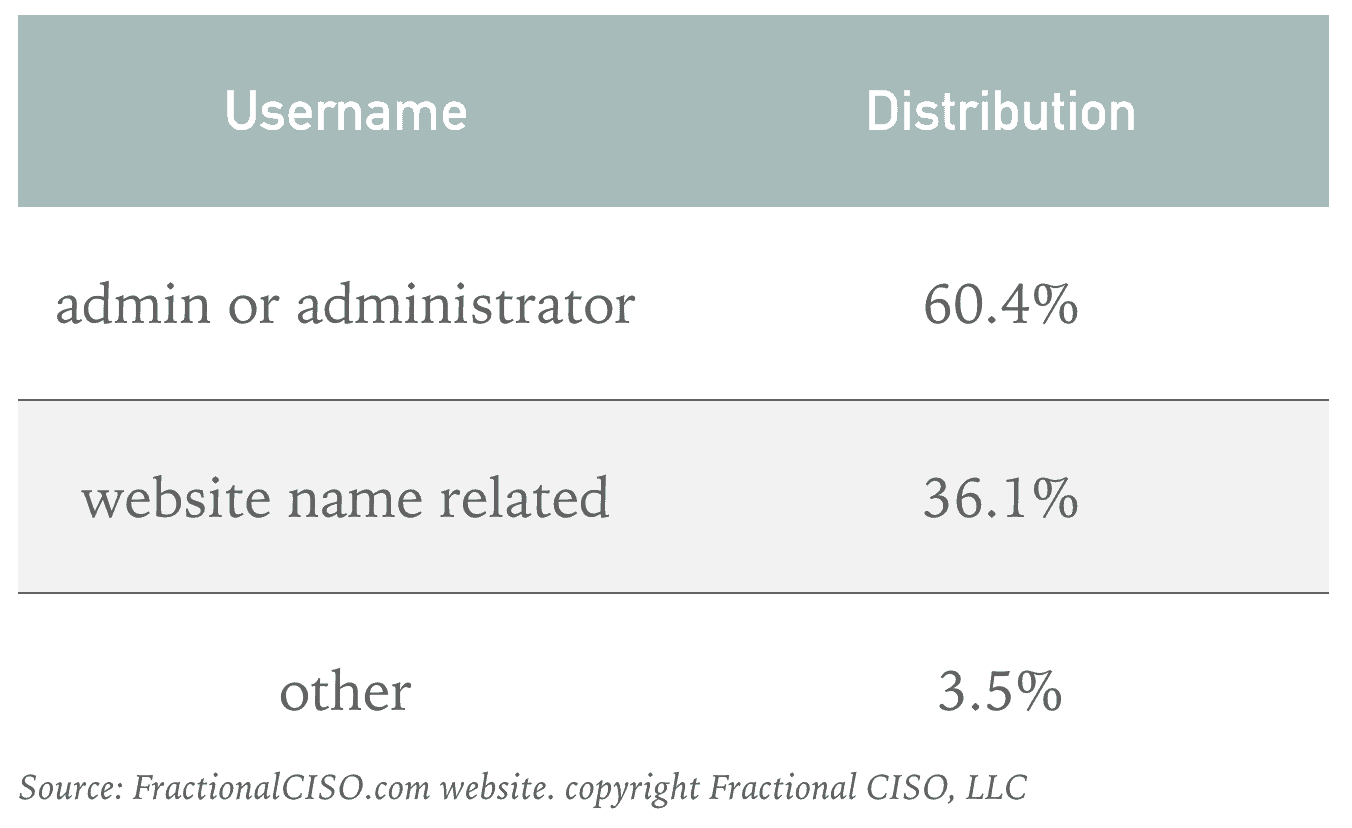
For a given week there are a large number of failed logins for administrative usernames that do not exist on the website. Presumably these are malicious attacks by outsiders. (We know that we didn’t unsuccessfully try to login.) Furthermore the distribution of those usernames is remarkably narrow. Sixty-plus percent of the failed logins use the ‘admin’ or ‘administrator’ username on the site. Many of the other usernames are website name related. Only a small percentage of the attempted hacks are with other types of logins. This week’s data was typical of the failed login data on the site.
From this data we can learn a lot about good username selection. Don’t create users with the admin or administrator name. Don’t create users with a variation of the website or system name. Additionally, although it is buried in other category don’t use ‘www’ or a name of one of the bloggers on the site.
Do you think that these recommendations are specific to one website? Looking at the data from other attacks such as the mirai botnet we can confirm that ‘admin’ or a variant is a common username attack. Eighty-five percent of the mirai usernames were ‘admin’, ‘administrator’, an admin variant, ‘root’ or ‘guest’. The mirai botnet was able to successfully attack thousands of devices trying only a small number of usernames.
Unlike password selection, username selection need not be complex. Pick a name, uncommon word or made-up word as your username. Simple preventative measures such as these can radically reduce the risk of website or system compromise.